Configuring secured connection to the LDAP server
When configuring the LDAP server connection, specifying LDAPS as a protocol will lead to encrypted connection using SSL/TLS. Supported SSL/TLS versions are SSL 3.0, TLS 1.0, TLS 1.1 and TLS 1.2. Because of the compatibility reasons, TLS 1.0 is enabled by default. It is highly recommended to enable only communication via TLS 1.2, since several weaknesses were found in the lower versions. For this, in the Dispatcher Paragon web interface, go to the System settings (Expert options) and find the cryptographicProtocolForLdapReplication property.
Also the list of ciphers used for LDAPS communication can be customized. This can be done by listing the cipher suites in customCipherSuitesForLdapReplication system property together with enabling allowCustomCipherSuitesForLdapReplication .
Server authentication
The authentication is ensured via SSL/TLS certificates. There are two options for certificate verification:
-
Comparison of the thumbprints - the first time Dispatcher Paragon connects to an LDAP server, the certificate hash is saved locally. Each next time this is compared to the one sent by the server.
-
Standard validation using digital signature - the server trust is validated the standard way, via checking the authority, validity and the server name matching.
With Expert options enabled, the "Mode of LDAP server certificate check" field is available and can contain two options: hash or secure.
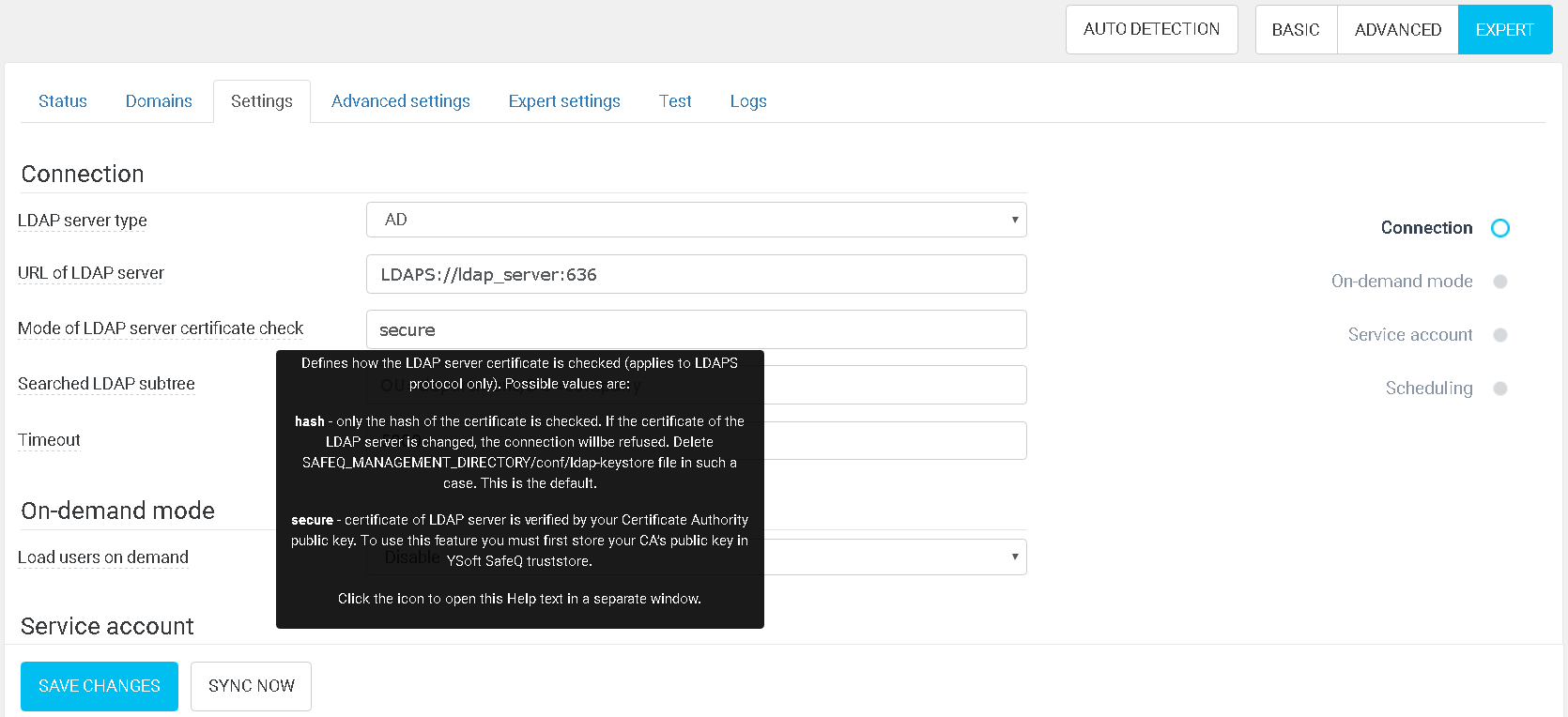
For the standard validation, the certificate authority needs to be present in the Dispatcher Paragon truststore. This ssl-truststore file can be found in the <management_folder>\conf\ folder. In case your LDAP server certificate is not signed by a publicly known authority, run the following keytool command to import it:
keytool -import -keystore ssl-truststore -file ldap_server_certificate.crt -alias ldap_server_certificateThe command will ask for a truststore password, which can be found in the <management folder>/tomcat/conf/server.xml file.